
Pilot Data Server Administrator Guide
Version PDS-9.1 | Published July 17, 2024 ©
Authentication
Roles
Pilot Data Server can be configured to use Authentication to control the access to Viz Pilot Edge, Template Builder and DataServerConfig.
There are 4 different roles defined:
-
pilot-journalist
-
pilot-editor
-
graphic-designer
-
pilot-admin
It is important to understand the distinction between roles and groups. Roles are what grants a user privileges, and a role can be assigned to a user directly, or to all members of one or more groups depending on the identity provider being used. The role names are fixed and defined by Vizrt, but you are free to define or reuse groups as you like.
These are the access rights for the different roles:
|
|
Viz Pilot Edge |
Template Builder |
Data Server Settings |
|
pilot-journalist |
|
|
|
|
pilot-editor |
|
|
|
|
graphic-designer |
|
|
|
|
pilot-admin |
|
|
|
Identity Configuration
Pilot Data Server uses the OpenID Connect Protocol (OIDC) to authenticate users. It can, in theory, be configured to integrate with any OIDC compliant identity provider.
The following providers have been tested and are supported:
-
Microsoft Entra ID (formerly Azure Active Directory)
-
Vizrt SSO (Keycloak)
Microsoft Entra ID
The Entra ID application configuration consists of two parts: an App Registration for the technical details of the application, and an Enterprise Application that defines user and group access and their role assignments, as well as other aspects of how the app integrates with your tenant.
To connect Viz Pilot to Microsoft Azure Entra ID (formerly Azure AD), log in to your tenant in the Azure Portal, then perform the following steps:
-
Go to the App Registrations blade.
-
Click New registration:

-
Type a name, for example Viz Pilot, and leave the other settings as is. Then click Register.
-
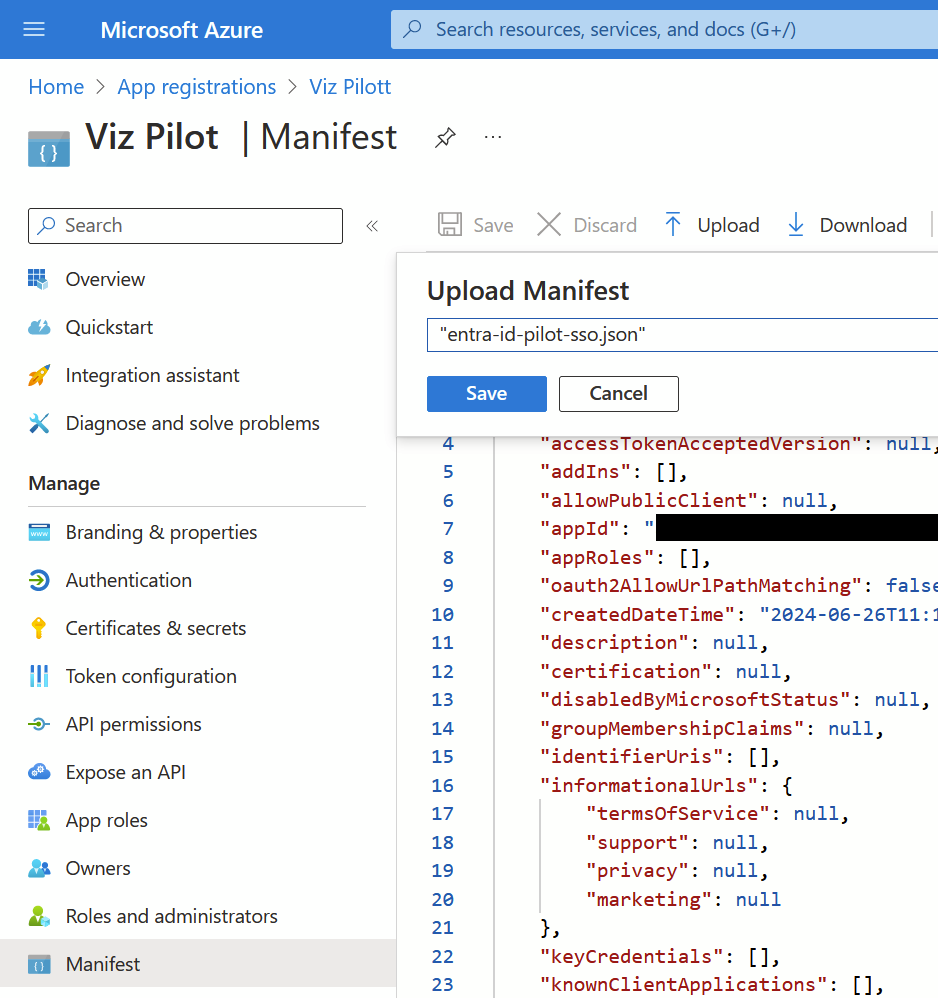
In the sidebar, click Manifest.
-
Click Upload, select the provided JSON file, then click Save.
-
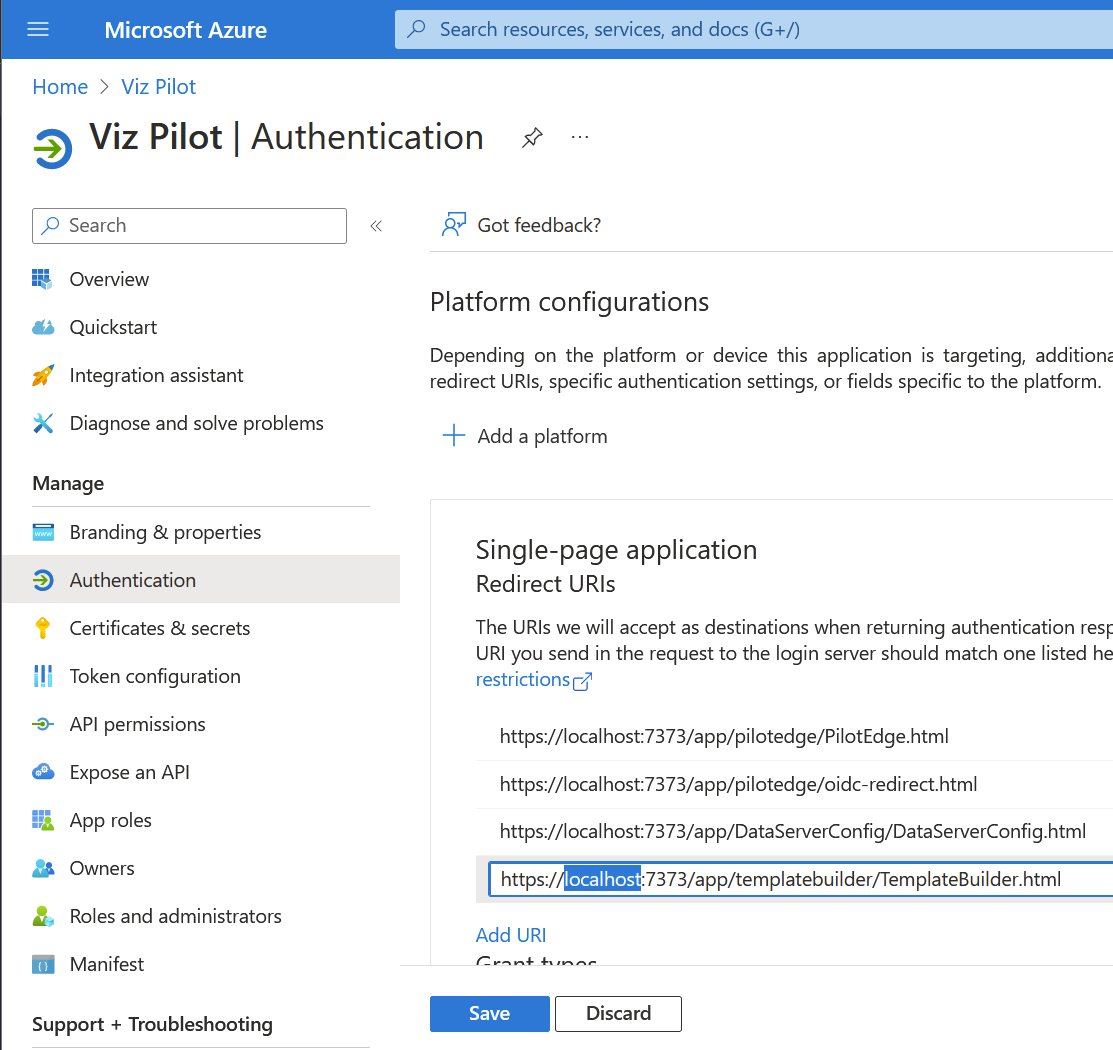
In the sidebar, click Authentication.
-
Edit the URLs to have the correct hostname, and click Save.
Optional:-
In the sidebar, click API permissions, then click Grant Admin Consent for <your tenant name>.
-
In the sidebar, click Branding & properties, then upload the provided logo.
-
In the sidebar, click Owners, then assign yourself and/or other users that should have access to manage this app registration.
-
-
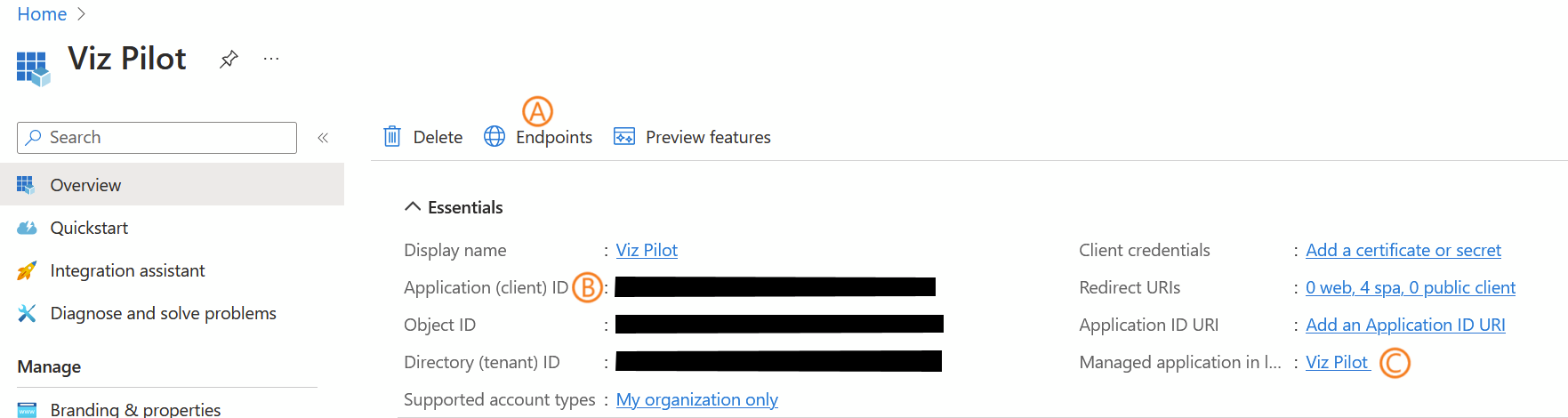
In the sidebar, click Overview:
-
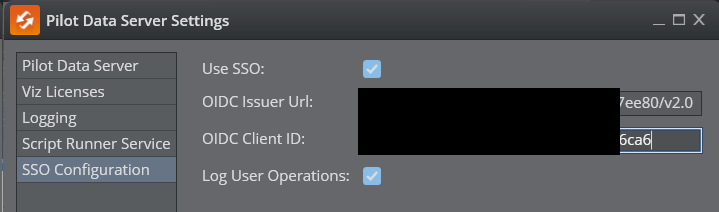
Open the Pilot Data Server Launcher, click Settings and select the SSO page (or use the notepad to collect the following values for a later entry).
-
Click Endpoints (A) and find the OpenID Connect metadata document field. Copy the left part up (but not including /.well-known/openid-configuration), and paste it into the OIDC Issuer Url field in Pilot Data Server Settings.
-
Find the Application (client) ID (B) value and copy it to the OIDC Client ID field in Pilot Data Server Settings.
-
Save the Pilot Data Server Settings and (re)start Pilot Data Server.
-
Click the link with the label Managed application in local directory (C), which takes you to the Enterprise Application blade.
-
Click Users and groups.
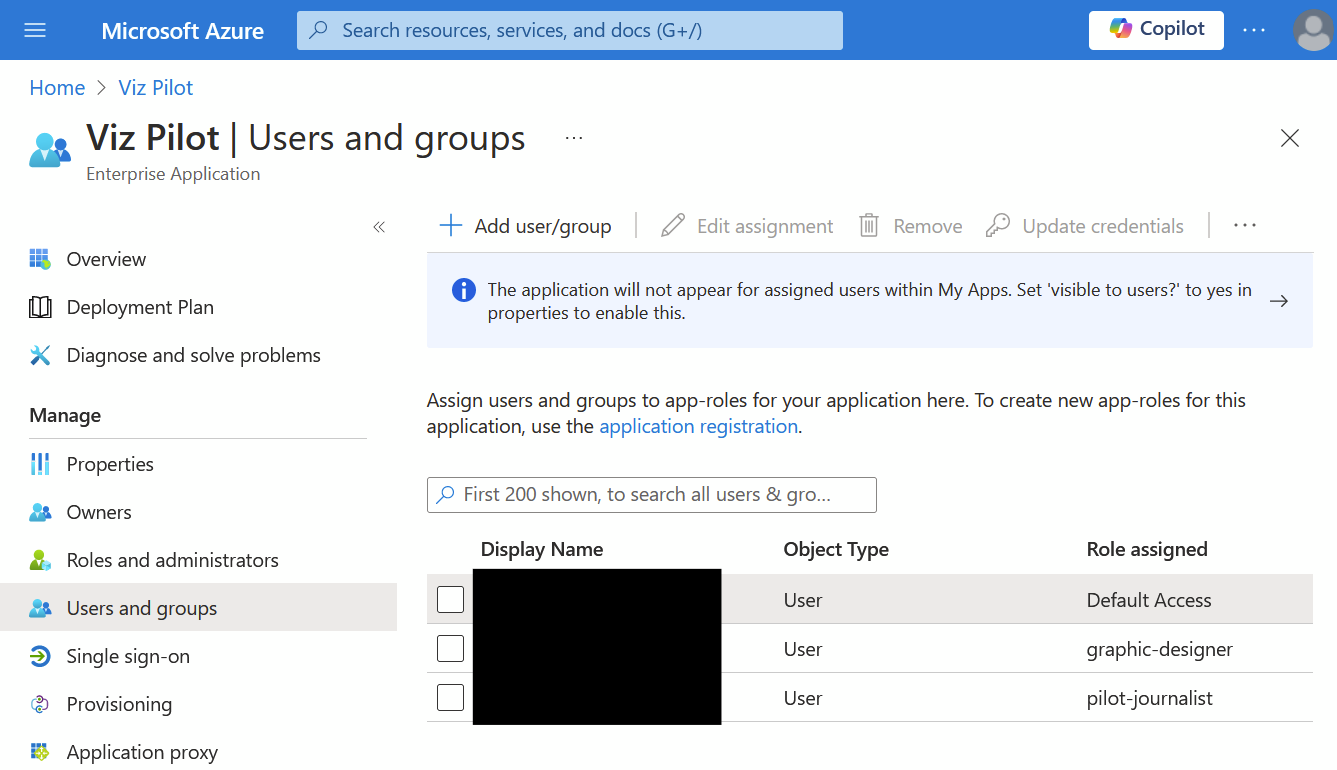
-
Add users and groups to roles as you wish (Default Access is added automatically but does not grant access to any Viz Pilot apps, so you may remove it).
-
You may also inspect the other pages in the sidebar to customize behavior and security, and assign other users that should have access to manage this Enterprise Application, as owners . You do not need to perform Provisioning for Viz Pilot.
Vizrt SSO (Keycloak)
To connect Viz Pilot to Vizrt SSO running in an existing Viz One deployment, perform the following steps:
-
Download the keycloak-pilot-sso.json file from the same folder that you got the installer on Vizrt’s FTP server.
-
Log in to the Viz One SSO Admin pages, and go to the Import tab in the left menu.
-
Click Select file and pick the keycloak-pilot-sso.json file.
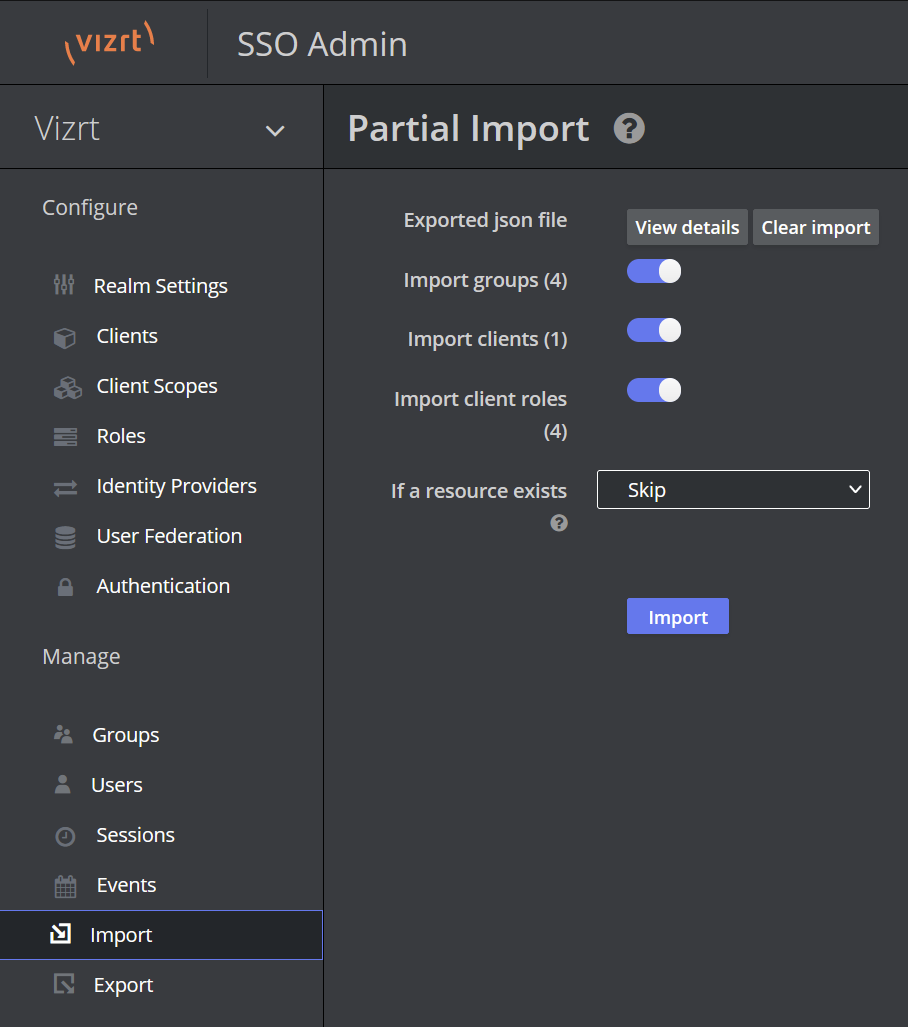
-
Review the options and click Import when ready.
-
Go to the Clients tab, find and open the VizPilot client that was just imported.
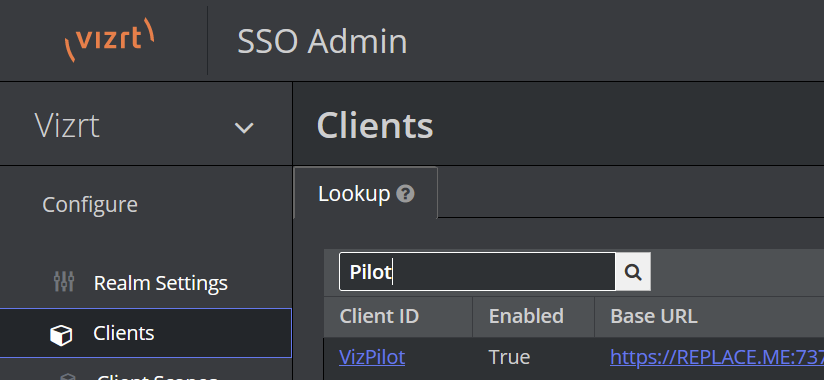
-
Update the Root URL field with the fully-qualified domain name of the Viz Pilot server. Also check and adjust the Valid Redirect URIs in case you have installed multiple versions of the web apps, or are using a reverse proxy with different path mapping or similar.
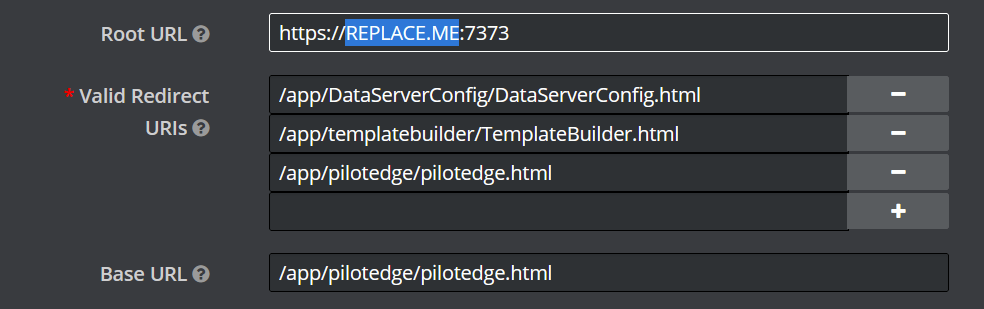
-
Manage users and groups to assign the four Viz Pilot roles as desired. The roles are defined by the VizPilot client, as shown in the screenshot below. The imported config includes example groups which you can use as-is, customize, or replace with your own groups. Remember that these groups don't directly grant any privileges, they just assign the corresponding roles to all group members, and it is the roles that grant a user privileges. The graphic-designer and pilot-editor roles also implicitly grant the pilot-journalist role. The pilot-admin role implicitly grants all the other Pilot roles.
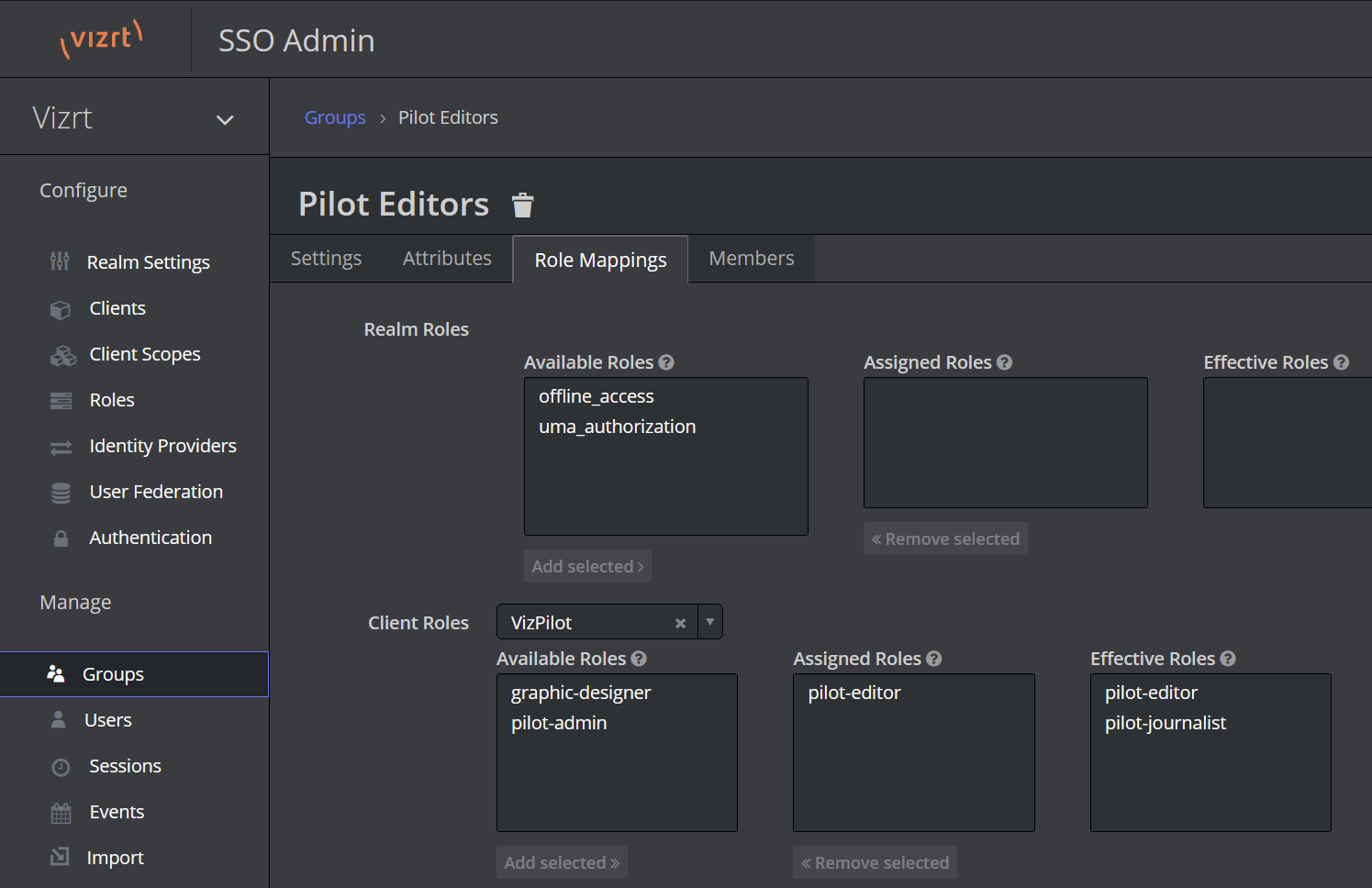
-
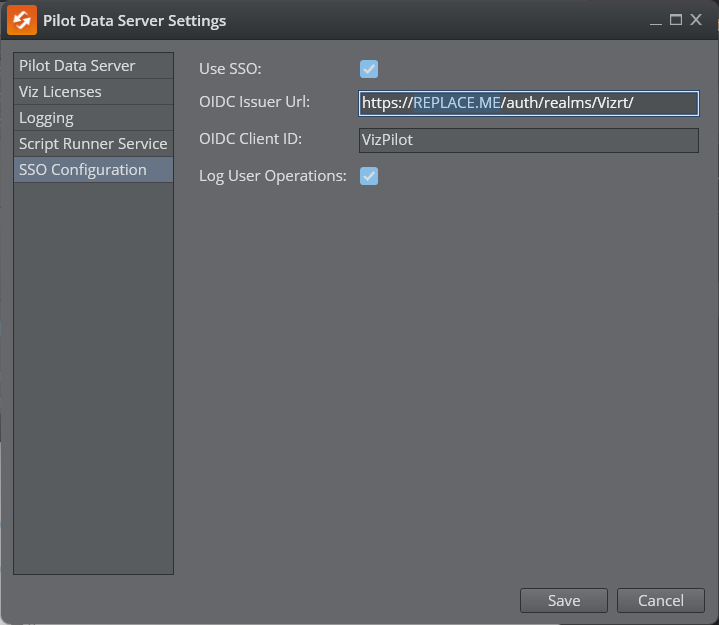
Use the Pilot Data Server Launcher to configure OIDC settings for the target server. The Issuer Url is typically the Viz One server's base url followed by /auth/realms/Vizrt. The Client ID should be VizPilot when using the imported config.
Newsroom Requirements
The Newsroom system hosts MOS plugins like Viz Pilot Edge in their own web browser environment. This environment must be considered secure by the authentication technology we are using in Viz Pilot Edge.
The following requirements must be met:
-
The newsroom web hosting environment for MOS plugins must communicate over secure socket (using the HTTPS protocol). This must be configured in the newsroom system.
-
The web browser hosting the MOS plugin guest must support popup windows to allow the login dialog to be displayed.
-
The web browser must support the SubtleCrypto web API as specified here: https://developer.mozilla.org/en-US/docs/Web/API/SubtleCrypto. All modern browsers support this API, but it may be that the newsroom system still deploys an older browser internally, which can be incompatible with modern authentication technology.
Known limitations per June 2024
-
The web browser in Avid iNEWS does not support popup windows. To use authentication in iNEWS, the ShowEdge wrapper must be used to host Viz Pilot Edge.