
Gateway Administrator Guide
Version 5.6 | Published May 15, 2024 ©
Secure Communication
As of MOS Protocol version 4.0.0, it is possible to configure the Gateway for secure web socket communication. Enabling secure communication between the Gateway, NRCS servers and control stations, the Media Sequencer hosting the Gateway requires set up with HTTPS.
This section describes setup and configuration of Gateway with a certificate for secure communication over web sockets. The recommended way to obtain a certificate is to request it from a Certificate Authority, though it is possible to use a self-signed certificate instead.
Prerequisites
Gateway
Install the Gateway as described in section Installation.
OpenSSL
OpenSSL is used to create a self-signed certificate, and the optional Diffie-Hellman group. The OpenSSL tool is only for creating the certificate files, it is not required to run Gateway.
The OpenSSL project does not distribute binaries, instead there are options for obtaining OpenSSL for Windows from a third party.
To install OpenSSL
A standalone installer for OpenSSL for Windows is available at https://slproweb.com/products/Win32OpenSSL.html.
-
Download and run the latest Light version of OpenSSL for 64-bit Windows (either EXE or MSI installer can be used).
Open an OpenSSL Command Prompt
After installing OpenSSL the tool will be available from an OpenSSL command prompt.
From the Windows Start menu navigate to the OpenSSL folder and click on the "Win64 OpenSSL command prompt" shortcut for opening a command prompt with the OpenSSL tool available.
Request Certificate from Certificate Authority
The recommended way of obtaining a certificate for the Gateway is to request it from a Certificate Authority (CA).
Usually your company will manage a CA on the company network, for example by using Microsoft Active Directory Certificate Services.
The procedure for obtaining a certificate may vary from company to company.
-
Use your company's procedure to request a web server certificate, for the machine hosting the Gateway.
-
The Gateway requires an X.509 certificate with separate certificate- and private key files in the PEM format.
Self-signed Certificates
It is also possible to use a self-signed certificate for secure communication to the Gateway.
However, this approach has the drawback that the certificate must be imported manually to all machines that needs to connect to the Gateway securely.
To create a self-signed certificate
-
Open a command prompt where the OpenSSL tool is available (see Open an OpenSSL command prompt).
-
At the command prompt, change the directory to the location where you want to store the certificate files.
In this example, you store certificate files in the data directory of the Media Sequencer hosting Gateway.> cd "%programdata%\Vizrt\Media Sequencer" -
Create a self-signed certificate. In this example, the certificate expires 365 days from now.
> openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout gateway-key.pem -out gateway-cert.pemThis command will generate a private key and certificate file in the current directory.
-
When prompted to provide company information, in the field Common Name, add the hostname used for connecting to the Gateway.
As this is a self-signed certificate you can leave the remaining fields blank.
To import a self-signed certificate
This procedure works for Media Sequencer control stations connecting securely to the Gateway and NRCS servers that use the trusted root certificate store for verifying certificates.
The certificate must be imported onto these client machines to enable connection of control stations and NRCS servers to the Gateway that has been configured with its self-signed certificate.
The certificate will be imported to the Windows trusted root certificate store.
-
Copy the self-signed certificate file to the client machine.
Note: Do not copy the private key or Diffie-Hellman group !
For security, these files must only reside on the Gateway. -
With an administrator command prompt, import the self-signed certificate for the Gateway:
(replace gateway-cert.pem with the path to your certificate file, if different)> certutil -addstore -f "Root" "gateway-cert.pem"
Configuring the Gateway
All configurations are made in the Media Sequencer initial menu.
HTTPS
Create a Diffie-Hellman Group
This step is optional, but recommended to increase security. It creates a Diffie-Hellman group file used to provide additional security.
-
From a command prompt where the OpenSSL tool is available (see Open an OpenSSL command prompt).
Note: This command has a long execution time (approximately 10 minutes).
-
'Use the following command to create a Diffie-Hellman group file in the current directory named "gateway-dhparam.pem".
> openssl dhparam -out gateway-dhparam.pem 4096Enable HTTPS
-
Open the Settings menu of the Media Sequencer launcher.
-
From the left-hand panel, select HTTPS.
-
Enable HTTPS.
-
Configure the HTTPS port.
-
Select the location of files for the certificate, private key and optionally a Diffie-Hellman group file.
-
-
Click Save.
-
(If the Media Sequencer is running)
You are prompted to restart the Media Sequencer for the changes to take effect.
Gateway Settings
Enable Secure Communication
-
On the MSE client, open the Gateway Controller (see Start the Gateway controller client).
-
Select the General Configuration tab.
This is where you configure the Gateway to use secure communication.
-
Enable Reject Insecure Connections to ensure all websocket connections to the Gateway are encrypted.
-
(Optional) You can enable Use Basic Authentication and specify a username and password required to connect to the Gateway over websocket.
Note: When Use Basic Authentication is selected, control stations and NCS servers must be configured to provide the username and password in order to successfully establish a connection to the Gateway.
Control stations and NCS servers must also connect to the HTTPS port for the Gateway instead of the default port for unencrypted HTTP. -
Apply the settings and restart the Gateway for the changes to take effect.
Configuring Control Stations
After setting up the certificate it should be possible to configure secure communication between the Gateway and the Media Sequencer running on the control station.
If you are using a self-signed certificate for the Gateway, make sure the certificate has been imported as explained in section Import a self-signed certificate.
MOS Config Web Application
Configure the Control Station Media Sequencer
-
Use the MOS config web application to configure the control station Media Sequencer (see Launch Standalone MOS Config Web-Application).
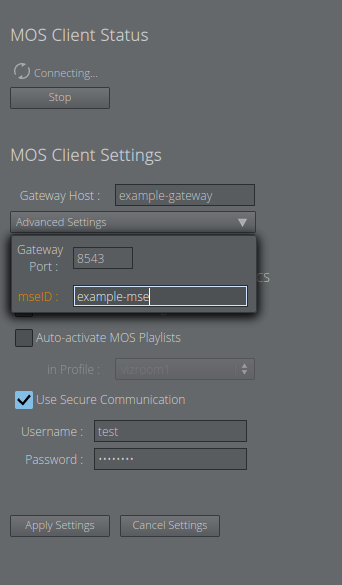
-
Configure the Gateway hostname, enable secure communication and provide the username and password configured for basic authentication against the Gateway.
If everything is configured correctly, the Media Sequencer should be able to establish a secure websocket connection to the Gateway.
Troubleshooting
-
If there are certificate errors when using a self-signed certificate, make sure the self-signed certificate has been imported on the control station.
-
If there are certificate errors when using a certificate from a certificate authority, make sure the client machine knows about the root certificate.
-
Verify that the client machine is connected to the domain.
-
Make sure the hostname used for connecting to the Gateway is the same as specified when the certificate was requested/created.